You must be logged in to view saved presets
Guided Walkthroughs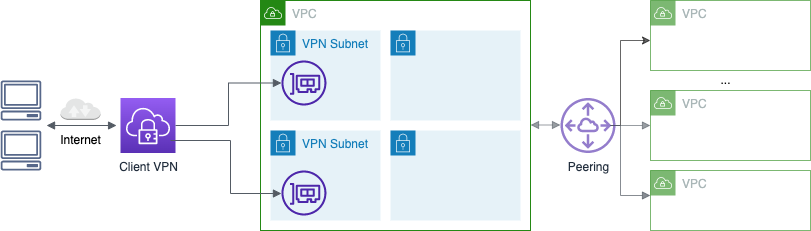
Client VPN Endpoint

Overview
This guided walkthrough is for configuring AWS Client VPN in an AWS account. The following can be deployed using this walkthrough:
- AWS Client VPN endpoints and configuring common Client VPN settings (such as session timeouts, self-service, DNS split tunnelling, etc.)
- Logging configuration for client connections
- Network settings such as routing for clients, VPN protocol and port, and DNS servers
- User authentication and authorization options (mutual TLS, active directory, and SAML2.0 federated authentication)
Consider the following items before starting with this walkthrough:
- An existing VPC is assumed to exist already. This Client VPN endpoints will be deployed in this VPC
- TLS Certificates are used for the Client VPN endpoint as well as for authenticating users (if mutual authentication is enabled). The walkthrough requires that these certificates already exist and are uploaded to AWS Certificate Manager (ACM)
- If Active Directory authentication is selected, then AWS Directory Service must be used and a directory must already exist in the account
A premium subscription is required for this content
Deploy
Client VPN Endpoint
Items
1
Size
0.5 KB
AWSTemplateFormatVersion: '2010-09-09'
Description: ''
Resources:
ClientVpnEndpoint:
Type: 'AWS::EC2::ClientVpnEndpoint'
Properties:
ClientCidrBlock: 192.168.0.0/22
ServerCertificateArn: ''
ConnectionLogOptions:
Enabled: false
ClientConnectOptions:
Enabled: false
TransportProtocol: udp
SplitTunnel: false
VpnPort: 443
SelfServicePortal: enabled
SessionTimeoutHours: 24
ClientLoginBannerOptions:
Enabled: false
Parameters: {}
Metadata: {}
Conditions: {}
